- Products
- Solutions
Solutions
Services
- Resources
- Customers
Explore CSC
Calabrio Success Center
Calabrio product training
- Partners
True-Cloud Enterprise-Grade WFOFind More Great Content- Customer Interaction Analytics
- Workforce Management
- Customer Experience
- Quality Management
- Contact Center Reporting
- Managing a Remote Workforce
Home » Workforce Optimization » Keeping Up with Contact Center Cloud Security
Keeping Up with Contact Center Cloud Security

We’ve finally passed the tipping point when it comes to contact center cloud security:
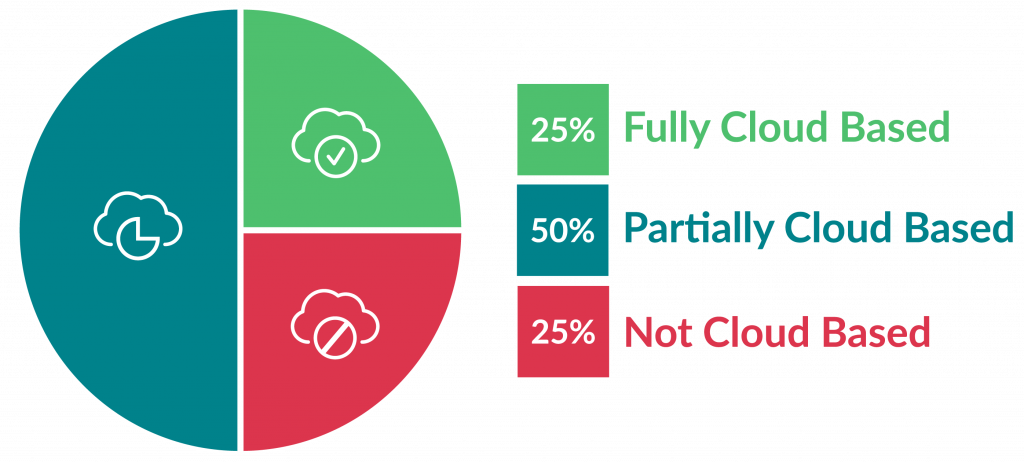
The apprehension that plagued it since its inception is dissipating as businesses of all sizes race to the cloud. Today, more than 75% of contact centers now have made full or partial moves to the cloud. And one-in-four are fully cloud-based.
The main reason why comes down to overcoming fears about data security. Contact center leaders everywhere now understand and believe data is significantly more secure in the cloud than it ever could be on premises.
In fact, our own State of the Contact Center 2021 report found 75% of contact centers say concerns about data security are no longer a barrier to cloud migration. Over the last five years, 50% of contact centers became less fearful about cloud security.
Contact center leaders today know that, compared to on-premises solutions, the cloud provides:
More comprehensive data security.The cloud offers better, more comprehensive types of data security that automatically stay up to date and protect all data, both at rest and in transit between apps, networks or users.
More secure data exchange.Leading cloud solutions are designed to optimize and secure the exchange of data via more granular authentication, more granular access control, and greater visibility and monitoring.
More robust technology developed by the best and brightest minds in data security.The top three cloud services providers (CSPs) — Amazon Web Services, Microsoft Azure and Google Cloud — attract and employ some of the smartest security experts in the world who continually develop better tools and protocols to protect cloud data against evolving threats.
Collective security insight from across the industry.Those three CSPs — along with many SaaS application providers — can more effectively, efficiently and continuously refine security protocols and best practices than any single contact center because they can independently monitor and analyze the collective, shared experiences of hundreds of thousands of client businesses.
It’s been a long time coming, but today’s contact center leaders finally acknowledge that controlling data by keeping it on prem doesn’t protect it more. That’s because insiders now pose the greatest risk to data security, with approximately 60% of all data loss caused — either maliciously or unintentionally — by authorized users. And it’s much more difficult for ill-intentioned insiders to access valuable, sensitive data when it’s stored in the cloud. (Plus, when anomalous activities and threats do occur, cloud-based contact centers can more easily identify and shut them down before they can cause damage.)
So now the conversation shifts. Before, reticent contact center leaders were asking why cloud contact centers were more secure than their on-prem counterparts; now, they want to know how to make sure to choose a truly secure cloud-based platform for their contact center operations.
Here’s what I tell them.
1. Pick a true-cloud solution, one that’s built for the cloud from the ground up…
(You don’t want an on-premises solution that’s been “adapted” to fit the cloud because it risks introducing to the cloud the data security gaps common to legacy systems.)
2. … on a major CSP …
(Smaller CSPs lack the expertise, innovation and resources of a major CSP like Amazon.)
3. … that comprehensively encrypts data …
(If it’s not comprehensive, it won’t protect all your data, everywhere, all the time.)
4. … integrates with identity management solutions …
(So your administrators can consistently control and monitor user access across all contact center systems.)
5. … allows for flexible, multi-factor authentication …
(So you can choose your authentication process and even add advanced, multi-factor authentication for increased security.)
6. … and can adapt to evolving data security regulations.
(So it can keep protecting data via adaptable data storage, control and security capabilities.)
As an enterprise-grade, true cloud contact center platform, Calabrio, of course, meets all the above criteria. But our overarching information security philosophy extends beyond preventing the unauthorized disclosure of data to individuals or systems — it’s also about assuring the accuracy and consistency of data over its entire lifecycle.
That’s why we’ve based our five-part information security program on the National Institute of Standards and Technology’s (NIST’s) cybersecurity framework. See more in Calabrio’s Trust Center:
- Identify — Conducts annual reviews to manage cybersecurity risks to systems, people, assets and data.
- Protect — Maintains identity management and access control (along with awareness and training programs) to support implemented technical measures covering data security.
- Detect — Facilitates timely discovery of cybersecurity events via continuous monitoring of information systems and assets, and detection and analysis of anomalous events.
- Respond — Maintains preparedness with activities like stakeholder communication, analysis, mitigation activities, and improvements from lessons learned that are in place and ready to activate when incidences are detected.
- Recover — Practices recovery exercises regularly to ensure systems or assets affected by incidents can be restored in the future.
A thorough, thoughtful and continuous approach to cloud contact center security is vital. Pick true-cloud WFO to make sure this is a given.
Tim is the Director of Information Security and Compliance at Calabrio. Tim has held leadership positions in Information Security at Ameriprise Financial, Deluxe Corporation, and Pine River Capital Management. He earned a master’s degree in Computer Engineering from Boston University. im enjoys hiking in the mountains and gardening with his family.Recent PostsCalabrio is a trusted ally to leading brands. The digital foundation of a customer-centric contact center, the Calabrio ONE workforce performance suite helps enrich and understand human interactions, empowering your contact center as a brand guardian.
We maximize agent performance, exceed customer expectations, and boost workforce efficiency using connected data, AI-fueled analytics, automated workforce management and personalized coaching.
Only Calabrio ONE unites workforce optimization (WFO), agent engagement and business intelligence solutions into a true-cloud, fully integrated suite that adapts to your business.
For customers and partners.
© Copyright 2024 Calabrio, Inc.7 Essential Elements of an Effective Corporate ProgramDebunking Common Data Security Myths with Calabrio’s Security ExpertsSend this to a friend - Solutions